Blog
- Home /
- Blog

Become a Cybersecurity Supercommunicator
This is the second post in a series on how to design, debug, reverse engineer, and deliver talks that land with impact in the high-stakes world of cybersecurity.
Read More
Cybersecurity Needs Supercommunicators
This is the first post in a series on how to design, debug, reverse engineer, and deliver talks that land with impact in the high-stakes world of cybersecurity. At the end of each post, you’ll find a ‘How to Coach for This?’ section.
Read More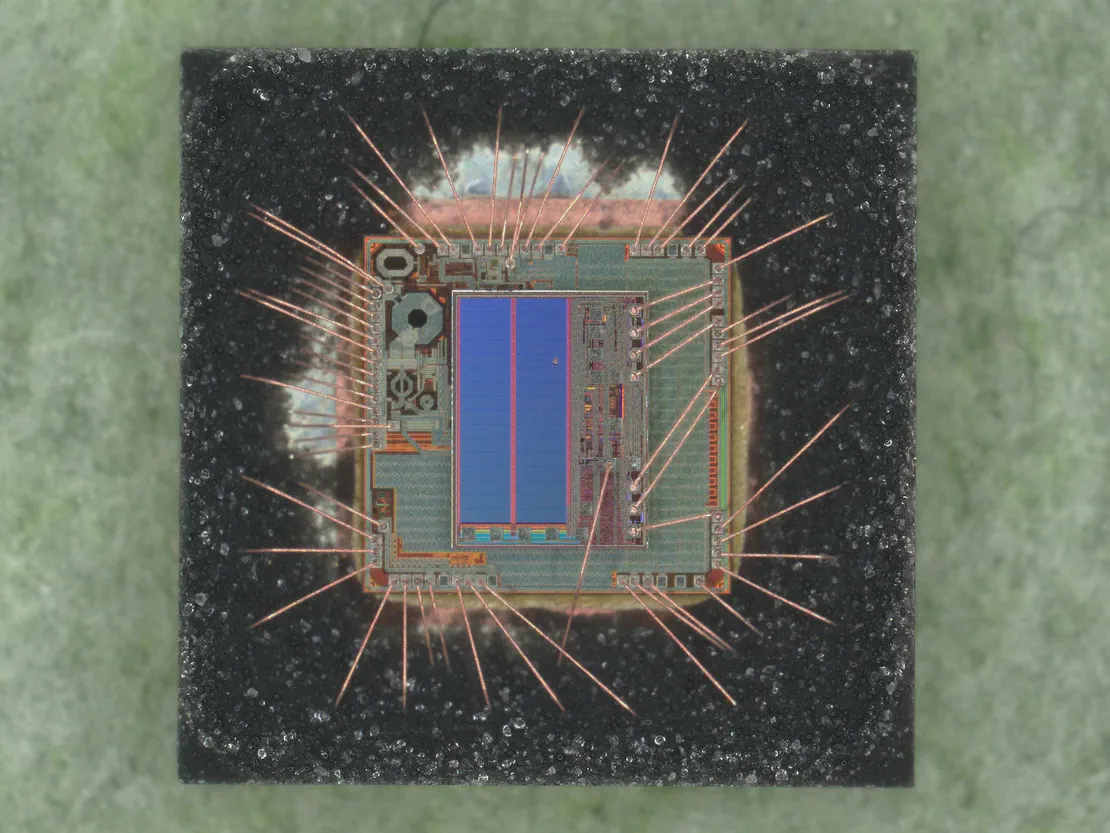
CPU Silicon Security Research and Fuzzing (RISC-V)
I’ve embarked on a brief journey to learn RISC-V and I ended up finding a niche of interesting material on security research on fuzzing, so I pivoted my attention to that. Here’s a brief summary of what I found.
Read MoreTeaching STEM Through Compound Machines
My son was asked to build a compound machine as science project. The machine is expected to dispense cards as a way to celebrate Valentine’s Day with classmates. I decided to “STEM+ the heck out of this project” and involve my son to let him practice with logic and fine manipulation skills.
Read More
Intel Alder Lake Leak Checker
Yesterday, the news broke that firmware code leaked from Lenovo, which included Intel Alder Lake reference code. While I leave you to this great post by Binarly.io’s REsearch team for the details, I want to focus on how to check if firmware images are affected.
Read More
Information and Cyber Security News Feeds
I want to release my very personal and opinionatedly organized infosec/cybersec sources in one OPML file. I don’t know to what extent I’ll be able to curate it, but for now I wanted to get it out.
Read More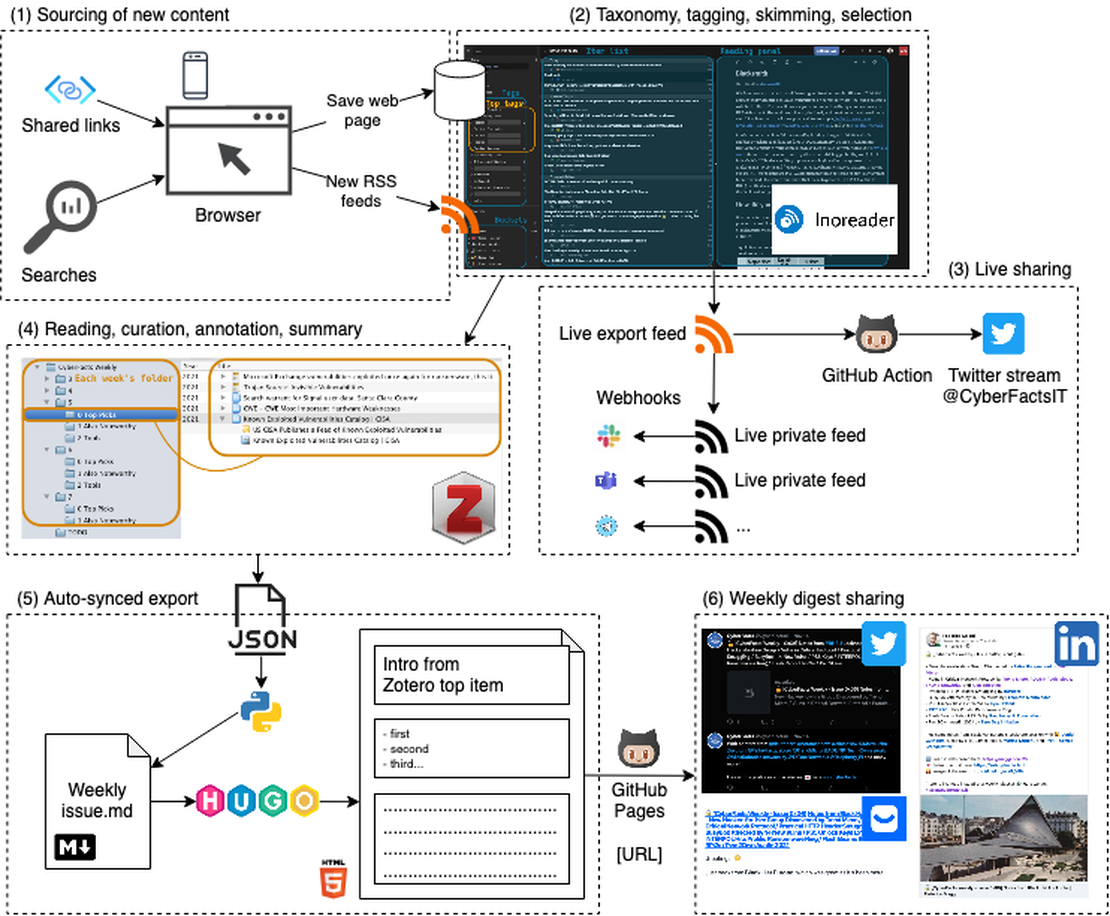
Scalable, Hand-curated Newsletters: A Data-centric, Automatic Workflow
I guess it’s not unique to the cyber-security world, but research and media move pretty fast here, so it’s easy to end up with hundreds of seemingly interestingly articles or blog posts to read every day. Of course, that’s not humanly possible. Let me tell you how I deal with this.
Read More
Masked Emotions
Despite this little beast known as COVID-19 pandemic is about to turn 1 year old, many people still feel strange when wearing masks. While wearing a face mask we can’t speak properly and we can’t see others’ mouth, so our experience of a conversation can change, especially if speaking is central in our lives (think of any public figure). Wearing a face mask impacts how we perceive others’ emotions as well as our emotions (how we feel). Because our own understanding of our emotions can also influence such emotions in a continuous feedback loop, the effect can go beyond how we feel in that particular moment.
Read More
Reading Aloud
Reading long texts has always been a daunting task to me. A rocky mountain I seldom find myself brave enough to start climbing (unless forced to). I’ve never had good reading habits, except for a few, very intriguing novels with a powerful storyline, which I could actually read quite fast. But most of the readings I wish I could get done quickly are damn hard. In the era of book-summarizing services like Blinkist, audiobooks, and “CEO reading guides,” where people invest time and money to compress time and read more, my limited reading abilities are an actual obstacle to my knowledge development. How did I change that? I don’t know if I did, but here is what I found by experimenting on myself.
Read More
Smart Manufacturing Security
How do we secure a smart manufacturing system, or a smart factory? Recent incidents such as the ransomware infection that halted production at a major semiconductor foundry in 2018 have already shown the impact of IT-to-OT lateral movement. Moreover, while smart manufacturing systems are isolated from other networks, there is a trend toward less isolation between IT and OT systems.
Read MoreCategories
- Anomaly Detection ( 1 )
- Arduino ( 1 )
- Automotive ( 1 )
- Communication ( 4 )
- Computer Vision ( 1 )
- Content Curation ( 1 )
- CVE ( 1 )
- Defacement ( 1 )
- Embedded ( 3 )
- Firmware ( 1 )
- Fraud ( 1 )
- Hardware ( 1 )
- Industrial ( 2 )
- Internet of Things ( 1 )
- Machine Learning ( 1 )
- Maker ( 1 )
- Malware ( 6 )
- Measurement ( 1 )
- Mobile ( 5 )
- Operational Technology Security ( 1 )
- Platform ( 1 )
- Psychology ( 2 )
- Ransomware ( 1 )
- Reverse Engineering ( 2 )
- RF ( 2 )
- Robotics ( 1 )
- Security ( 11 )
- Silicon ( 1 )
- STEAM ( 1 )
Tags
- Android
- Arduino
- Black Hat
- Boot
- Cars
- Chipsec
- Covid
- DCL
- Defacement
- DIMVA
- DNS
- Eletronics
- Embedded
- Espionage
- Firmware
- Fuzzing
- IIoT
- Industrial
- Intel
- Iot
- Italian
- Italy
- Lenovo
- Malware
- Measurement
- Mobile
- Motivation
- Paper
- POLIMI
- Privacy
- Psychology
- Radio
- Ransomware
- Reading
- RF
- Routers
- SDR
- Security
- STEAM
- Trend Micro
- Trendmicro
- Vulnerability
- Web
- Webinject
- Workshop
- Youth