Blog
- Home /
- Blog
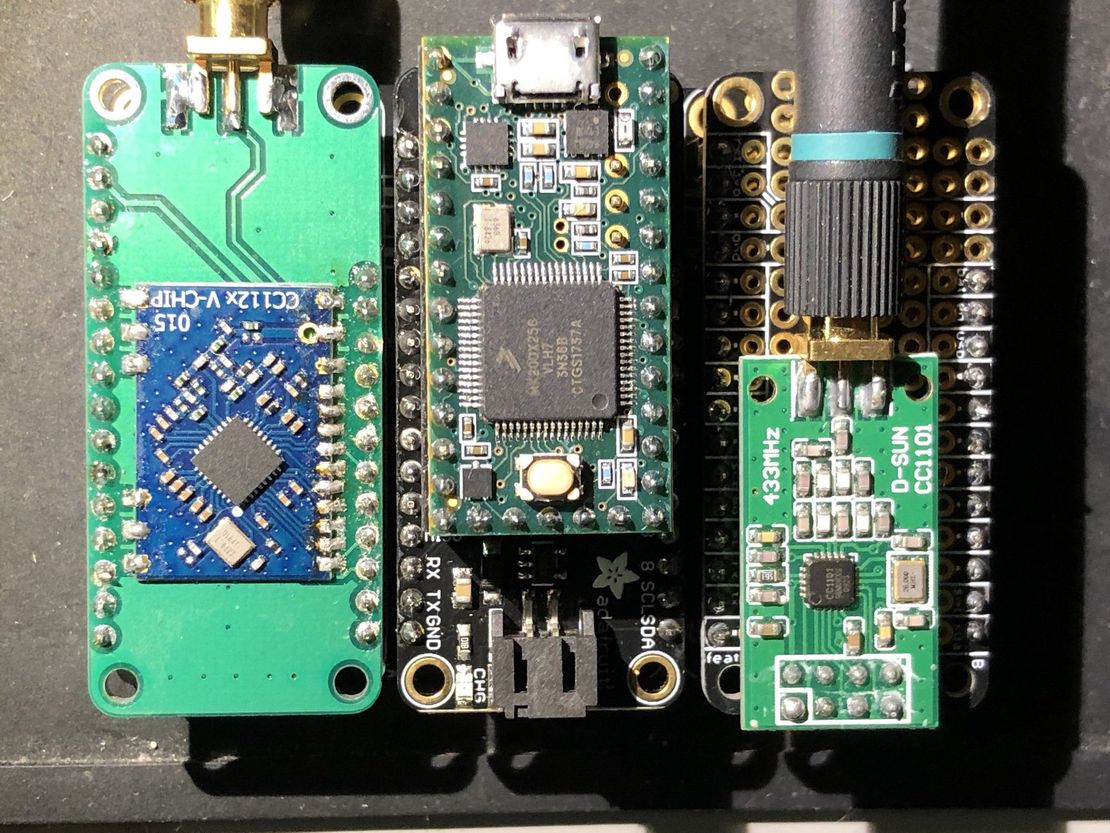
RFQuack: the versatile RF-analysis tool that quacks!
RFQuack is the only versatile RF-analysis tool that quacks! 🦆 RFQuack is the evolution of a prototype to help me reverse engineer sub-GHz and 2.4GHz RF protocols based on digital packet radios.
Read More
Radio Killed the Radio Stars: Security Analysis of RF Protocols for Industrial Applications
After having analyzed the several RF protocols for industrial applications, distributed by global vendors, we discovered that none of them had sufficient security features to prevent an attacker from hijacking the communication and manoeuvre the controlled connected machines.
Read More
Large Scale Analysis of Defaced Web Pages
Given the multiple releases around this topic and project, I’ve decided to put together a summary. So far, there is: a tool, a white paper, an academic paper, and (spoiler alert) another white paper coming soon.
Read More
Dnsmasq and CVE-2017-1449*: A Reality Check and Remediation Practices
Many vulnerabilities in one shot, yet several pre-conditions for a target to be actually exploitable. Here’s simple flowchart to check whether your Dnsmasq deployments are vulnerable.
Read More
Robosec: Industrial Robot Security
Industrial robots are complex cyber-physical systems used for manufacturing, and a critical component of any modern factory. Besides the mechanical arm, inside an industrial robot there are not just electromechanical components but a multitude of complex embedded controllers.
Read More
From a Bit-flipping to a Vulnerability in the CAN Standard
CAN-based protocols are vulnerable to bit-flipping attacks at the link layer. In this collaborative research, Politecnico di Milano’s NECSTLab and Trend Micro’s FTR analyze the protocol in depth and demonstrate the vulnerability on a real car, with PoC and so on.
Read More
Prometheus: Automatic signature generation for WebInject-based banking trojan detection
The goal of this project is to extract signatures that capture the WebInject behavior of trojans. WebInject-based trojans are still the most popular e-crime tool.
Read More
The Role of Industrial Routers in Keeping the Future Factory Secure
Industrial routers play a very crucial role: a single vulnerability can grant the attacker access to an entire network of critical machines. In this research, I’ve looked at how easy it is for a hypothetical attacker to find and enumerate industrial routers, and the security posture of their vendors.
Read More
What we Know About Eyepyramid
The day before the EyePyramid case exploded, I received a confidential email with a PDF. It was the scanned copy of the court order for the law enforcement to proceed and arrest the Occhionero brothers. In a few minutes, I noticed that this leaked document was also circulating on various private mailing lists and chat groups I’m part of. At some point, I received a non-redacted copy.
Read More
Mobile (Android) Ransomware
I’ve started this project while advising a Master student who was interested in machine learning. As I’ve been using machine learning since around 2006, I was immediately hooked by the idea of using it to determine whether an Android app was trying to lock the target device as part of a ransomware scheme.
Read MoreCategories
- Anomaly Detection ( 1 )
- Arduino ( 1 )
- Automotive ( 1 )
- Communication ( 4 )
- Computer Vision ( 1 )
- Content Curation ( 1 )
- CVE ( 1 )
- Defacement ( 1 )
- Embedded ( 3 )
- Firmware ( 1 )
- Fraud ( 1 )
- Hardware ( 1 )
- Industrial ( 2 )
- Internet of Things ( 1 )
- Machine Learning ( 1 )
- Maker ( 1 )
- Malware ( 6 )
- Measurement ( 1 )
- Mobile ( 5 )
- Operational Technology Security ( 1 )
- Platform ( 1 )
- Psychology ( 2 )
- Ransomware ( 1 )
- Reverse Engineering ( 2 )
- RF ( 2 )
- Robotics ( 1 )
- Security ( 11 )
- Silicon ( 1 )
- STEAM ( 1 )
Tags
- Android
- Arduino
- Black Hat
- Boot
- Cars
- Chipsec
- Covid
- DCL
- Defacement
- DIMVA
- DNS
- Eletronics
- Embedded
- Espionage
- Firmware
- Fuzzing
- IIoT
- Industrial
- Intel
- Iot
- Italian
- Italy
- Lenovo
- Malware
- Measurement
- Mobile
- Motivation
- Paper
- POLIMI
- Privacy
- Psychology
- Radio
- Ransomware
- Reading
- RF
- Routers
- SDR
- Security
- STEAM
- Trend Micro
- Trendmicro
- Vulnerability
- Web
- Webinject
- Workshop
- Youth