Security
- Home /
- Categories /
- Security

Become a Cybersecurity Supercommunicator
This is the second post in a series on how to design, debug, reverse engineer, and deliver talks that land with impact in the high-stakes world of cybersecurity.
Read More
Cybersecurity Needs Supercommunicators
This is the first post in a series on how to design, debug, reverse engineer, and deliver talks that land with impact in the high-stakes world of cybersecurity. At the end of each post, you’ll find a ‘How to Coach for This?’ section.
Read More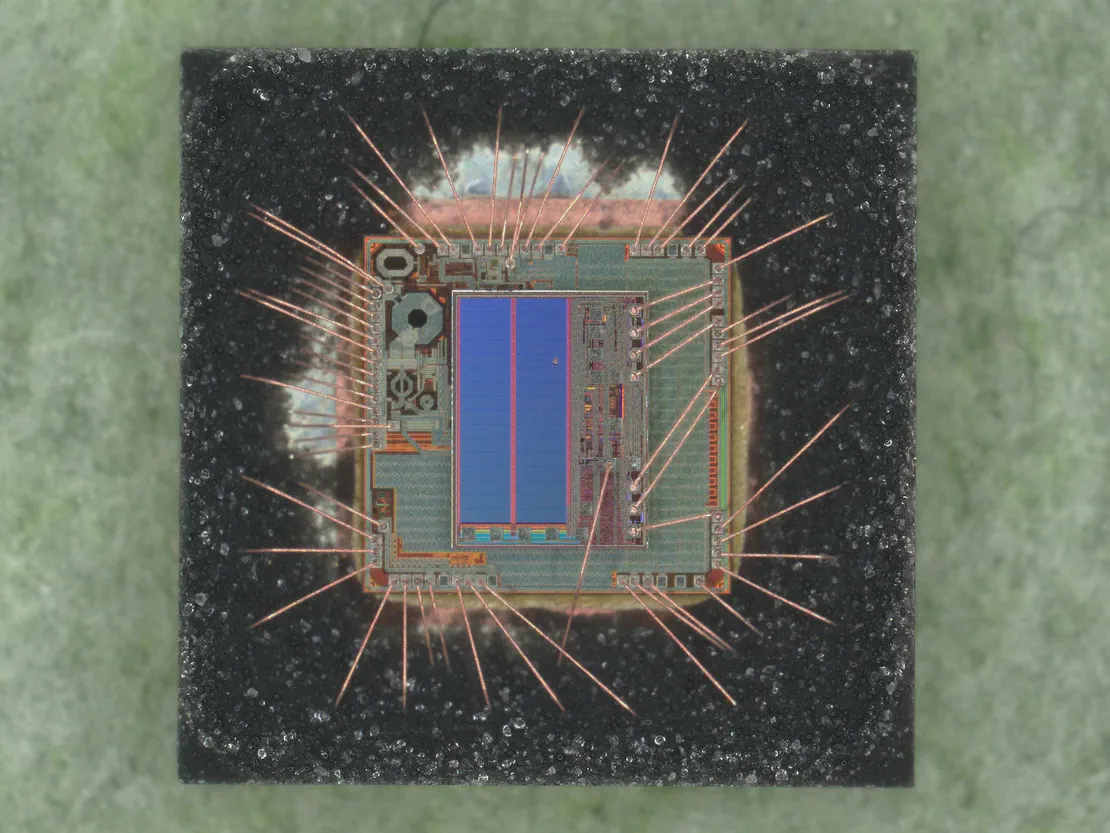
CPU Silicon Security Research and Fuzzing (RISC-V)
I’ve embarked on a brief journey to learn RISC-V and I ended up finding a niche of interesting material on security research on fuzzing, so I pivoted my attention to that. Here’s a brief summary of what I found.
Read More
Intel Alder Lake Leak Checker
Yesterday, the news broke that firmware code leaked from Lenovo, which included Intel Alder Lake reference code. While I leave you to this great post by Binarly.io’s REsearch team for the details, I want to focus on how to check if firmware images are affected.
Read More
Information and Cyber Security News Feeds
I want to release my very personal and opinionatedly organized infosec/cybersec sources in one OPML file. I don’t know to what extent I’ll be able to curate it, but for now I wanted to get it out.
Read More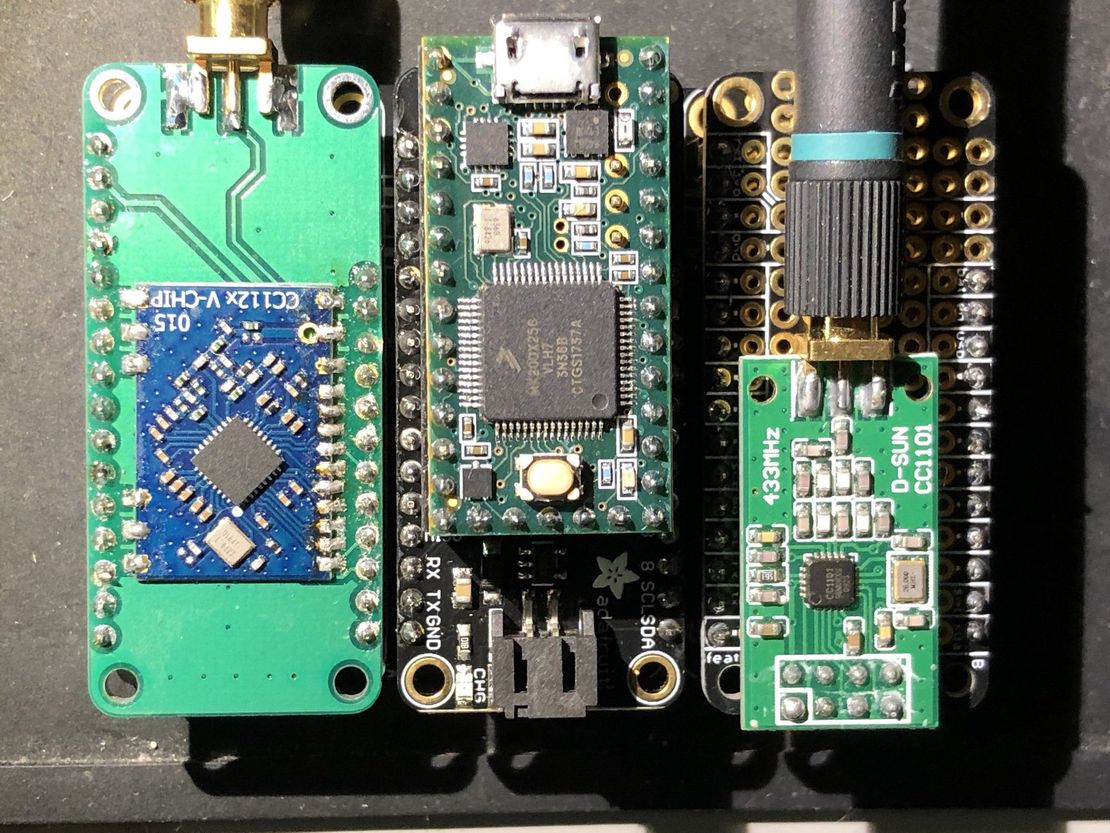
RFQuack: the versatile RF-analysis tool that quacks!
RFQuack is the only versatile RF-analysis tool that quacks! 🦆 RFQuack is the evolution of a prototype to help me reverse engineer sub-GHz and 2.4GHz RF protocols based on digital packet radios.
Read More
Dnsmasq and CVE-2017-1449*: A Reality Check and Remediation Practices
Many vulnerabilities in one shot, yet several pre-conditions for a target to be actually exploitable. Here’s simple flowchart to check whether your Dnsmasq deployments are vulnerable.
Read More
Robosec: Industrial Robot Security
Industrial robots are complex cyber-physical systems used for manufacturing, and a critical component of any modern factory. Besides the mechanical arm, inside an industrial robot there are not just electromechanical components but a multitude of complex embedded controllers.
Read More
From a Bit-flipping to a Vulnerability in the CAN Standard
CAN-based protocols are vulnerable to bit-flipping attacks at the link layer. In this collaborative research, Politecnico di Milano’s NECSTLab and Trend Micro’s FTR analyze the protocol in depth and demonstrate the vulnerability on a real car, with PoC and so on.
Read More
The Role of Industrial Routers in Keeping the Future Factory Secure
Industrial routers play a very crucial role: a single vulnerability can grant the attacker access to an entire network of critical machines. In this research, I’ve looked at how easy it is for a hypothetical attacker to find and enumerate industrial routers, and the security posture of their vendors.
Read MoreGrab 'n Run: Secure dynamic code loading for Android
A simple and effective Java Library that you can easily add to your Android projects to perform secure dynamic class loading operations.
Read More